The ongoing cyberattack in Ukraine affected the websites of ministries of foreign affairs, education, agriculture, ecology, regional development, sport, internal affairs, energy. as well as the sites of the State Treasure, the State Emergency Service, and the Digital Transformation Ministry's web service Diia.
- Read also: Everything you need to know about the massive Petya cyberattack which started from Ukraine (2017)
At the same time, the websites of the Ministry of Health, the Ministry of Internal Affairs, the Ministry of Social Policy, the Ministry of Infrastructure, and the Ministry of Finance operate normally. The sites of the Defense Ministry and the Security Service weren't affected by the attack as well.
About 10:00, the Ministry of Digital Transformation of Ukraine published their statement on Telegram, assuring that personal data weren't stolen, and stating that most of the affected websites were restored,
"Most of the attacked state web resources have already been restored. The content of the sites remained unchanged, and no personal data were leaked. Other sites will resume in the near future," the statement reads.
Most of the affected websites checked by Euromaidan Press at the time were offline.
What we know about the hack
The website of the Ministry of Education and Science and other official sites were defaced (defaced pages on Web Archive: the MFA, Education Ministry, Agrarian Ministry), displaying an image with an anti-Ukrainian threat clumsily written in three languages - Ukrainian, Russian, and Polish. Hackers rewrote the code of the original pages, embedding the image in the document itself using the so-called data URI scheme rather than linking the image from an external location. The content of some pages was fully rewritten, while the MFA homepage included the malicious javascript code to replace the original contents of the homepage with the same deface image.
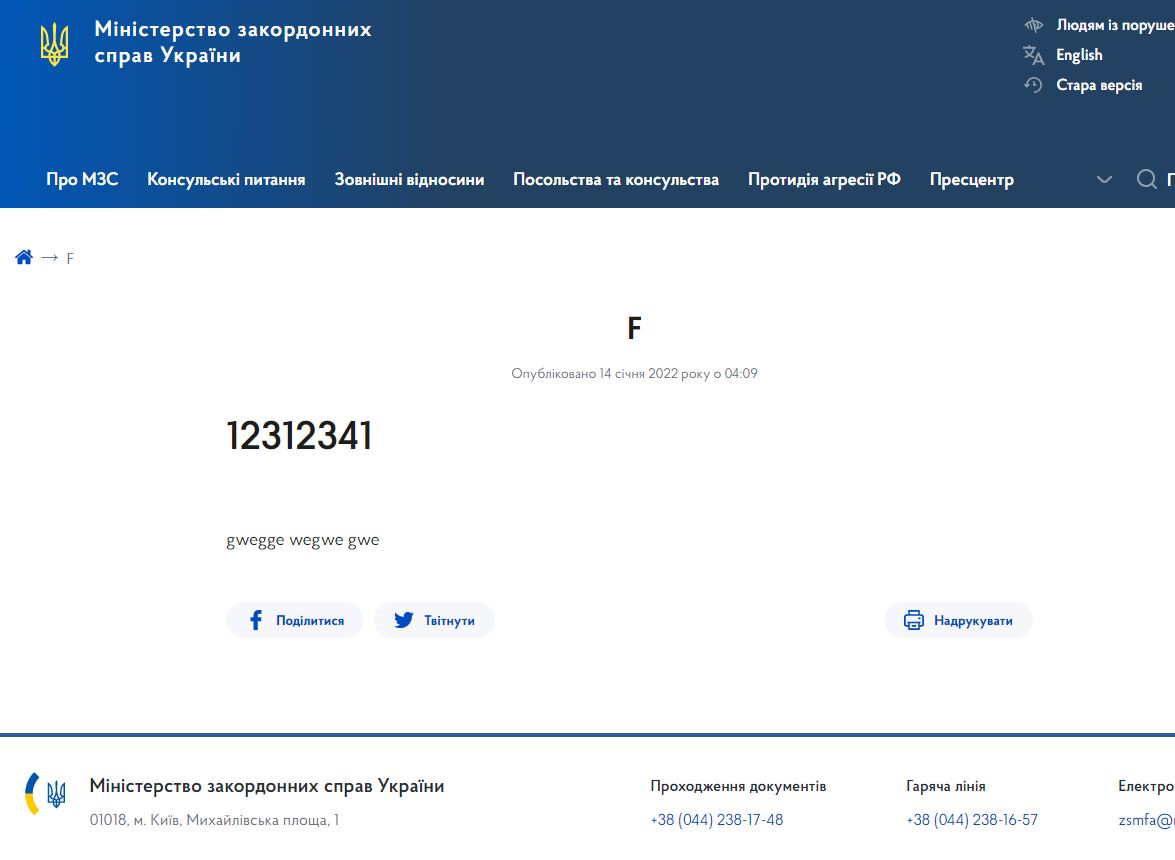
The threat in the deface image reads,
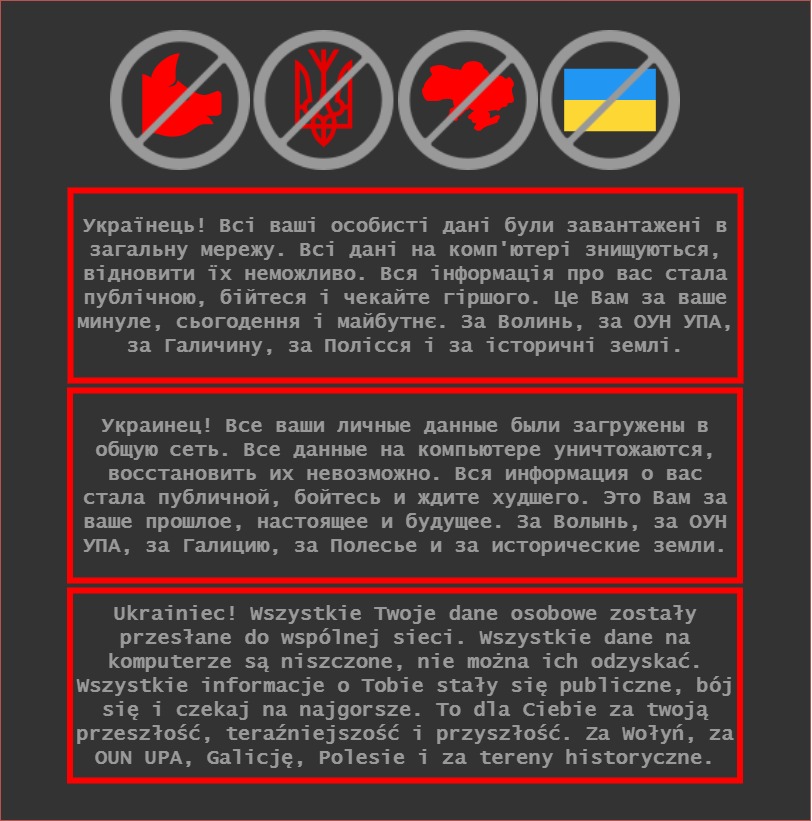
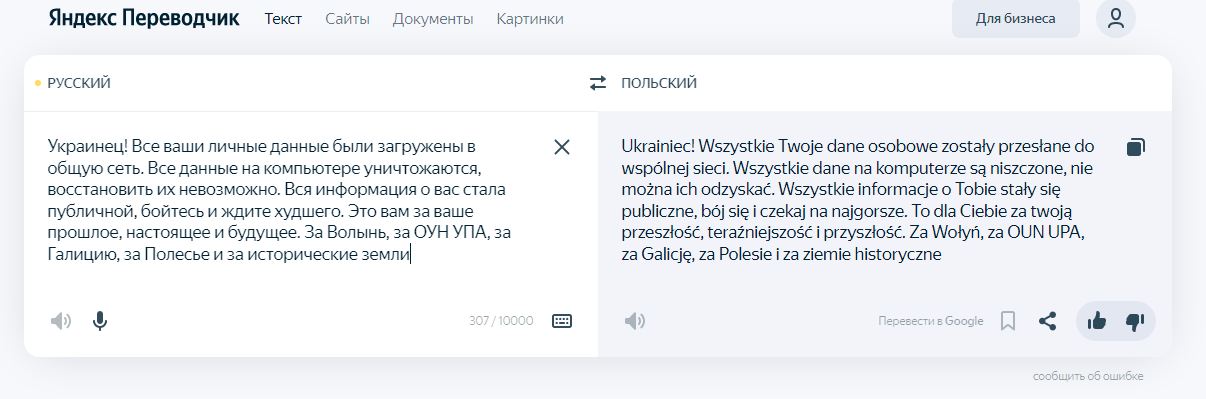
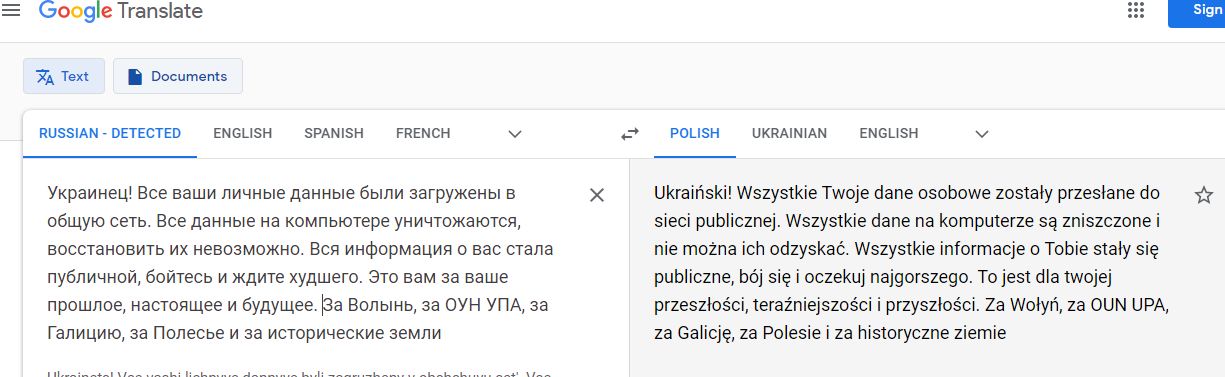
"Ukrainian! All personal data of y'all were uploaded to the public net. All the data on the computer are being destroyed, it is impossible to restore them. All the information about you has become public, be afraid and wait for the worst (or worse in the machine-translated Ukrainian version - Ed.). It is for you for your past, present, and future. For Volhynia, for OUN UPA, for Galicia, for Polissia and for historic lands (or territories in the Polish version, - Ed.)."
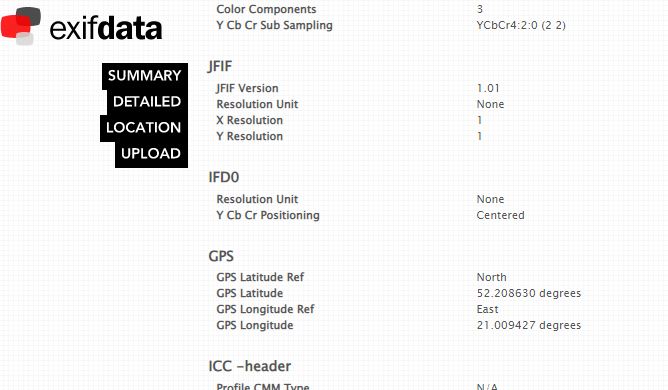
To make sure that the picture makes an even more obvious Polish connection, the hackers added the so-called Exif data to the image, showing the alleged location where the photo was taken. The provided coordinates show a random car parking lot in Warsaw:
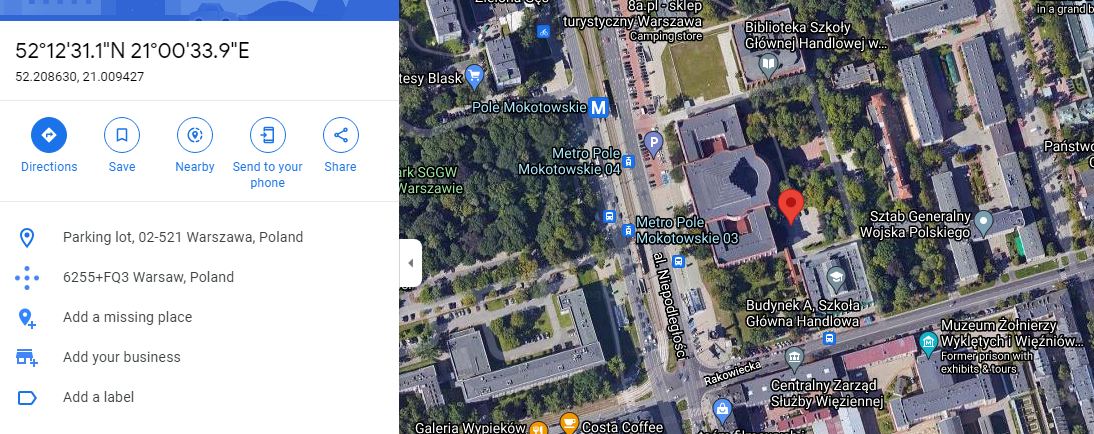
As of 12:00 Kyiv Time of January 14, most of the affected government websites were shut down, while the homepage of the Diia service showed the message that the Service was temporarily unavailable:

Hackers allegedly used Russian service Yandex Translate for translations
The deface image left by the hackers on the Education Ministry's website gives some hints regarding the hackers.
A simple comparison of the machine translations of hackers' Russian-language text produced by Google Translate and the Russian service Yandex Translate shows the nearly identical translation into Ukrainian in both, except for one conjunction in the last sentence.
However, Google's Polish machine translation from Russian is way different from the Polish version shown in the deface image, while the hackers' Polish text is nearly identical to the translation by Yandex, except for one noun in the last sentence.
The same goes for the machine translation from Polish into Russian and Ukrainian on Yandex, where the original Russian version is identical to Yandex's translation, and the Ukrainian one differs by one word in the last sentence. Meanwhile, Google produces much different Russian and Ukrainian versions when translated from the hackers' Polish text.

The Ukrainian version smoothly translates into the image's Russian text on both Google and Yandex translates, yet Google's Polish translation from Ukrainian differs a lot, while Yandex's is identical to that in the deface image except for the word tereny, which also is the only difference in Yandex's Russian-Polish translation from the original Polish version of the threat.
Threat text's author isn't a native Ukrainian or Polish speaker
The threat message left on official sites by the hackers implies its "Polish footprint," yet the text's author is doubtfully a Polish or Ukrainian speaker.
As we mentioned earlier, the use of the conjunction "і" in the last sentence of the Ukrainian text isn't stylistically correct according to euphony rules as it goes after a word that ends with a vowel, an error which is pretty hard to make for a native speaker.
European Pravda points that instead of the vocative case, the first word is used in the nominative in both Polish and Ukrainian versions, which is possible in Ukrainian, but not in Polish.
Reporting on the cyberattack in Ukraine, the Polish site Wprost doesn't seem to have liked the translation quality of what seems to be Yandex's machine translation into Polish, they wrote,
"Content in Polish is written in a way that suggests that a not very good translator was used."
European Pravda talked to Polish natives who explained that some phrases in the Polish text look artificial and built up in a way that Polish speakers would never formulate them. For example, "...zostały przesłane do wspólnej sieci" should be "zostały opublikowane w sieci" and so on.
Reaction
Most of the Ukrainian officials either withheld their comments so far or just reported the face of the cyber attack on the official sites, while experts and social media users were more eloquent in their comments.
The Ministry of Education and Science recommended in their Facebook post using their social media pages, while cyberpolice was investigating the case, and the work to resolve the site issues were still underway.
The Foreign Ministry also encouraged to use its Facebook and Twitter pages, while Ministry's spokesperson Oleg Nikolenko reported on his Twitter that sites of MFA and other agencies were down due to a "massive cyber attack,"
As a result of a massive cyber attack, the websites of the Ministry of Foreign Affairs and a number of other government agencies are temporarily down. Our specialists have already started restoring the work of IT systems, and the cyberpolice has opened an investigation.
— Oleg Nikolenko (@OlegNikolenko_) January 14, 2022
EU Foreign Minister Josep Borrell has condemned cyberattacks against Ukrainian government websites and said the EU's Political and Security Committee and cyber units would meet to discuss how to respond and help Kyiv.
NATO Secretary-General Jens Stoltenberg has also condemned the attack, according to the RFE/RL editor:
NATO Sec gen condemns the cyber attacks on #Ukraine and adds that “NATO & Ukraine will sign an agreement on enhanced cyber cooperation, incl Ukrainian access to NATO’s malware information sharing platform. NATO’s strong political and practical support for Ukraine will continue.”
— Rikard Jozwiak (@RikardJozwiak) January 14, 2022
The social media users discovered the attack on Ukrainian official websites around 1 AM. One of the early comments on the fact of the attack by opposition journalist Maria Madzihon reads,
"Hackers have hacked the government site of the Education Ministry mon.gov.ua. And this government is still offering us their "electronic voting" as in Russia, God forbid!"
"In fact, something like this was to be expected," wrote the Ukrainian hacktivist known as Sean Townsend of the Ukrainian Cyber Alliance, who had earlier criticized the lax approach of the officials to cyber security. He also pointed that the Kremlin's news agency RIA Novosti published their news piece on the attack at night only two hours after the beginning of the attack.
Head of Defense Reform Center Oleksandr Danyliuk attributed this attack to Russians, saying that it is part of a Russian hybrid operation aimed at:
- demonstrating Ukraine's vulnerability;
- undermining the West's position at the talks with Russia;
- worsening Ukrainian-Polish relations;
- possible discrediting government officials responsible for cybersecurity and their further replacement with Russian agents of influence.
The Ukrainian Embassy to Japan backed the opinion that Russia was behind the cyberattack, according to BBC Ukraine,
"It seems to originate in Poland. In fact, there is no doubt that this is another provocation by Russia," the Embassy wrote on their Facebook page, according to BBC Ukraine. However, Euromaidan Press couldn't find the original post, which could have been deleted sometime afternoon.
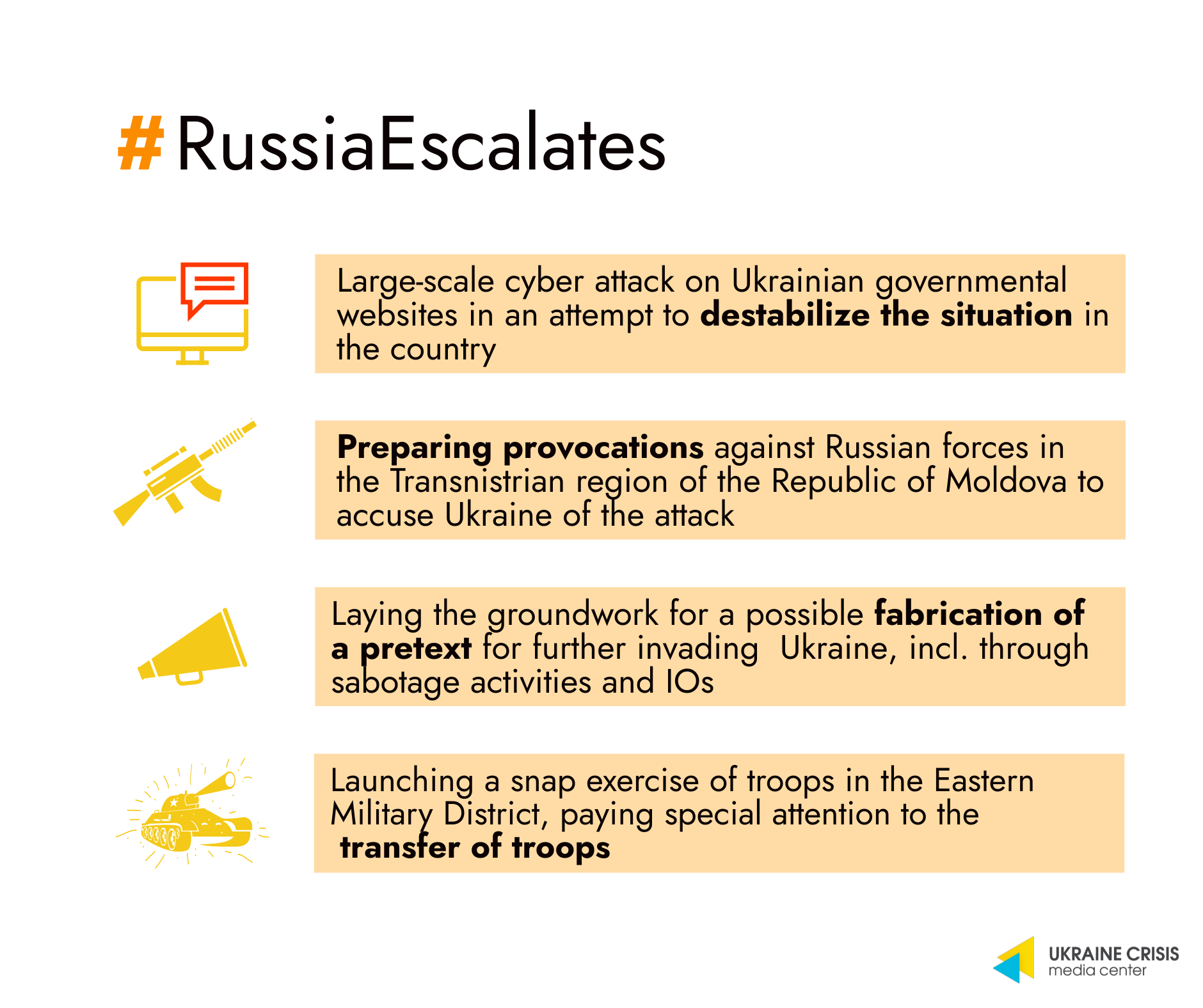
The Center for Strategic Communications (StratCom) of Ukraine has published its statement saying that the purpose of such attacks is "to destabilize the internal situation in the country, as well as to sow chaos and despair in society."
Cyberattacks on government agencies are a regular occurrence in Ukraine, though the Center points that there wasn't such a massive attack for a long time now.
"We assume that the current one is connected with Russia's recent defeat in the negotiations (with the US and with NATO, - Ed.) on Ukraine's future cooperation with NATO. The other day Moscow resumed military exercises near Ukraine's borders. And hacking actions against Ukrainian government agencies may also be part of this psychological attack on Ukrainians," the statement reads.
StratCom also says that the timeline of spreading the news reports on the cyberattack in Ukraine points to the Russian trace as well:
"The information first appeared on social media, then the first publications in the media were on 'drain tanks' (fake news media used to initial disseminating of desired narratives, - Ed.). And then it was actively spread by Russian news outlets... And only in the morning, the news story was picked up by the Ukrainian media," the StratCom statement reads.
A cyberattack in Ukraine was not unexpected
The Security Service of Ukraine previously reported that in December 2021 alone it had prevented 59 cyber attacks on information systems of public authorities. And in the first half of last year, the agency reportedly "neutralized more than 1000 cyber attacks and incidents" on web resources of the government and critical infrastructure.
The New York Times reported in late December 2021 that the United States and Britain had quietly sent cyberwarfare experts to Ukraine,
"Not an invasion with the 175,000 troops he (Russian President Putin, - Ed.) is massing on the border, but cyberattacks that take down the electric grid, the banking system, and other critical components of Ukraine’s economy and government," the NYT article reads.
Update 20:55:
The sales of electronic insurance policies have been suspended indefinitely in Ukraine, according to Autogeek.com.ua, referring to social media users, claiming that the suspension occurred due to a malfunction of the services of the Motor Transport Insurance Bureau. Namely, the compulsory car insurance database reportedly went offline "due to an external attack." Moreover, according to some information, Autogeek.com.ua speculates, the MTIB bases could have been destroyed by hackers. It wasn't immediately clear whether the reported attack actually has been taking place or is just speculation spread by social media users. If the attack was real, it is still unclear whether it's part of the massive cyberattack on Ukrainian government sites.
Update 21:18:
The Computer Emergency Response Team of Ukraine (CERTU) by Ukraine's State Service of Special Communications and Information Protection (Derzhspetszvyazok) has published its take on the cyberattack on Ukraine's official sites.
"The content of the sites was not changed and the leakage of personal data, according to preliminary information, did not occur," the agency says.
CERTU reported that many websites of government agencies were temporarily suspended to prevent the spreading of the attack and localize the issue, meaning that many of the official websites inaccessible on 14 January weren't affected by the attack.
The agency says that one of the possibilities for the attack was exploiting a known vulnerability in the October CMS installed on the official websites. In recommendations for site administrators, the agency recommends upgrading to a newer version of the CMS, which implies that a number of official websites haven't been updated to the latest version of the site content management software by now.
Update 16:00, Jan 15:
- In total, more than 70 government websites were under attack overnight into 14 January 22, with 10 of the attacked sites suffering from unauthorized interference, according to a statement by Derzhspetszvyazok.
Derzhspetszvyazok says that there is a high probability that the attack was the so-called supply chain attack, i.e. initially the attackers hacked the infrastructure of a commercial company that had administrative access to the web resources affected by the subsequent attack.
According to Ekonomichna Pravda, this company was Kyiv-based Kitsoft, which was involved in the development of nearly 40 government sites, using the October CMS. As of 15 January afternoon, Kitsoft's website was offline.
The authentication bypass vulnerability in the CMS was known since May 2021, patched in August 2021. The administrators of the affected websites didn't install critical updates by the time of the attack.
https://twitter.com/haynesdeborah/status/1482257253835096064?fwp
Update 20:50, Jan 15:
Reuters says that Serhiy Demedyuk, deputy secretary of Ukraine's National Security and Defense Council, told them that Ukraine blamed the 14 January attack on a group known as UNC1151, linked to the intelligence of Russia's ally, Belarus. According to the official, the group used malware similar to that was earlier used by a group tied to Russian intelligence.
Further reading:
- Germany has good chance to secure new EU anti-Russian sanctions for cyberattacks
- Why are Russian hackers targeting COVID-19 vaccine laboratories?
- The Kremlin’s cyber contractors. Their motives and risks
- Russia-linked cyber attacks targeted 104 accounts of European think tanks (2019)
- Ukrainian hackers turn on own government to make it care about cybersecurity (2018)
- Everything you need to know about the massive Petya cyberattack which started from Ukraine (2017)
- Ukrainian banks, enterprises, media and energy companies under powerful cyber attack, including Chornobyl NPP – LiveUpdates (2017)
- Moscow expanding its cyber war against Ukraine (2016)
- Cyber attacks have not hindered elections — SBU (2014)

