Euromaidan Press verified the information. It turns out that the hack is most probably authentic, but it is impossible to completely verify the most compromising messages.
Hack and finds
On 7 April, NGO Myrotvorets Center published the fourth part of their "Operation Regata" alleging they have discovered and confirmed the fact that the campaign of the leader of the Ukrainian presidential race, Volodymyr Zelenskyy, was partially funded by Russia via a cryptocurrency trading site owned by a former pro-Russian mercenary in the Donbas. The proof came from an e-mail box on the Russian webmail service mail.ru, which Myrotvorets hacked and monitored for an unknown period of time.
The NGO shared the dump of the email account so that anyone can check and validate the e-mail messages. Moreover, Myrotvorets provided videos showing the process of the validation of the messages which contain a DKIM e-signature and explaining how to validate messages when the email body was reformatted during forwarding.

The e-mail box [email protected] belongs to Dmitry Khavchenko, who was born in Crimea and later had a business in Kyiv. In 2014, he helped the Russian occupation forces in Crimea and later joined the pro-Russian terrorist forces in the Donbas. There, Myrotvorets claims, he was one of the pro-Russian militants who handed over the black boxes of Malaysian flight MH17, shot down over the occupied territory of the East-Ukrainian region on 17 July 2014, to Malaysian experts. In 2015-2016, Khavchenko served as "an officer of the special operation department of the DNR prosecutor general's office."
In 2017, Khavchenko moved to occupied Crimea where he established and headed the local office of the so-called "Union of the Donbas Volunteers" (SDD). In the second half of 2018, Khavchenko became an owner of a bankrupted cryptocurrency exchange BTC later renamed into WEX
. Myrotvorets states that he acquired the platform with the assistance of the Russian secret service - the Federal Security Service (FSB).
"My idea is to make Wex a platform for funding the unrecognized republics [of DNR, LNR, Transnistria, Abkhazia, and South Ossetia]. Our goal is fighting the dominance of the dollar," according to Khavchenko's explanation why he had bought the service as cited by the Russian service of BBC.
The email dump contains correspondence dated starting from 2006 to 23 March 2019. And among the messages throughout the years up to 2019 were personal letters to friends and family members, confirmations of orders in internet stores, medical test results from a lab in Kyiv, lots of sent and received photographs from vacation travels. Newer messages contained DNR operational documents, photos, and personal details of members of the illegal armed formations in the Donbas. And the newest messages show Khachenko's activities as an SDD leader.
One of the addressees is [email protected], who signs his letters as Andrey Yurievich. Myrotvorets identifies him as Andrey Pinchuk (Yurievich is a patronymic, not the last name), an FSB colonel residing in Russia, who earlier worked in the "MGB of PMR" or "the Ministry of State Security by Transnistrian Moldovan Republic" and later as a "DNR MGB deputy minister," according to Myrotvorets.
The NGO states that the frozen funds of WEX were used to back FSB operations starting from late 2018 and that Khavchenko executes "immediately, fully, in full obedience" the orders of Pinchuk about managing the funds.
"...Khavchenko's email box we had control of wasn't main, but a reserve [communication channel]," states Myrotvorets, and the several important messages got there "due to either glitches or temporary disruption of the standard communication channels between [Khavchenko] and Pinchuk. It often happens when Pinchuk visits a locality with an unstable connection, and he travels much, from Yekaterinburg to Havana, and from Belgrade to Aleppo."
Three above-mentioned messages dated 25 February 2019 contain what is allegedly an order to cash and hand over money to representatives of Ukrainian presidential candidate Volodymyr Zelenskyy for campaigning, confirmation of the readiness to execute the order, and notification one of the local offices of the amount of money.
Here are the screenshots and translation of the messages:
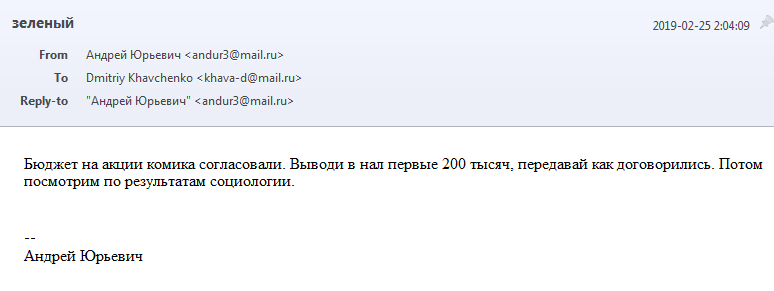
Date: 2019-02-25 00:04:09 UTC
Subject: Green [the last name Zelenskyy is derived from zelenyi "green"]
From: Andrey Yurievich <[email protected]>
To: Dmitriy Khavchenko <[email protected]>
Reply-To: "Andrey Yurievich" <[email protected]>
Message: The budget for actions of the comedian has been approved. Withdraw the first 200,000 to cash, hand over as agreed. Then we'll consider by the results of the sociology.
Date: 2019-02-25 11:07:14 UTC
Subject: Re: Green
From: Dmitriy Khavchenko <[email protected]>
To: Andrey Yurievich <[email protected]>
Reply-To: "Dmitriy Khavchenko" <[email protected]>
Message: Received. I will start the withdrawal of the crypto tomorrow, and it will go to that side during the [current] week.
Date: 2019-02-25 11:07:14 UTC
Subject: Contract4
From: Dmitriy Khavchenko <[email protected]>
To: [email protected]
Reply-To: "Dmitriy Khavchenko" <[email protected]>
Message: 4 200
The last mentioned email address can be found on the official site of the Zelenskyy campaign where it is listed as the contact address of the Mykolaiv regional office:
We have contacted the headquarters and the Mykolaiv office of the Zelenskyy's campaign via email asking them to comment whether they had received the abovementioned message and how they interpreted it if they had. At the moment of publication, we have received no response. The article will be updated if we receive any comment.
The Myrotvorets Center has published on its website
and sent an open letter to Ukrainian security structures - the National Security and Defense Council, the Security Service of Ukraine, and to the Verkhovna Rada's Committee for the Issues of the National Security and Defense. The letter lists the discovered facts and urges to take emergency decisions:
"Taking into account that the mentioned actions of the Russian special services which carry a threat for the security of Ukraine, we inform you [about the mentioned facts] for taking urgent decisions by the National Security and Defense Council of Ukraine, the Security Service of Ukraine, and the Verkhovna Rada of Ukraine.
In light of the public significance of the information on the funding the campaing of Zelenskyy by the Russian special services and meddling by the aggressor country in the Ukrainian electoral process discovered by the Myrotvorets Center, the acquainted materials and the circumstances around discovering them have been published on the websites myrotvorets.news and ordilo.org," reads the 7 April statement.
Validation
There is no doubt that the hacked email box is genuine since the huge array of the email messages on various topics shows the routine correspondence of a person throughout more than 10 years. The messages contain lots of personal details, contacts, photographs, and documents. A number of the messages contain DKIM e-signatures and can be validated directly or after reformatting the base64-encoded message body to fix the mail.ru bug which can emerge when a message is automatically forwarded to another mailbox.
We couldn't independently verify the identity of Andrey Pinchuk and the fact that he owns the email box [email protected].
The DKIM-headers missing from emails sent from mail.ru doesn't mean that the messages are fake. It just highlights the fact that we cannot verify them by checking their DKIM Signature.
The box also contains messages which were sent and received within the period when the three mentioned messages were delivered, as well a month later on, up to 23 March. The newest non-spam or mailing list message is dated 15 March, and the most recent reply followed on 16 March. The two messages contain a routine conversation with a former DNR militant about his hardships after he finished his service due to a permanent disability owing to a combat injury, the militant asks for help and Khavchenko as a representative of a "DNR veteran organization" gives his an advice in his reply. Thus, the email address was used by its owner for at least two and a half more weeks since the date of the emails in question.
Christo Grozev of Bellingcat has pointed out that two options still remain in which Zelenskyy campaigners can still be innocent of the raised accusations:
The hacks are authentic, I checked them out. Seems like there could be only two innocent (for Ze) explanations: (1) Russia/DNR emailed this on purpose to discredit Ze's campaign, or (2) Myrotvorets themselves sent the email to Ze's campaign. Both unlikely, but must be checked.
— Christo Grozev (@christogrozev) April 7, 2019
We cannot independently neither refute nor approve the pieces of evidence surfaced by the Myrotvorets Center. Only the SBU could make it all clear by checking the workers of the Mykolaiv office of the Zelenskyy campaign whether they were connected to receiving any cash money after the notification message was allegedly sent on 25 February, as well as the agency could check the email box whether it contained any earlier similar notification messages from other email address(es) and what was the reaction of them.
Reputation of Myrotvorets
The Myrotvorets Center NGO was earlier widely criticized by media and human right protection organizations, however, the criticism referred to the personalities Myrotvorets added to its database and wasn't linked to the validity of the hacked documents the center had shared.
As we mentioned in our previous article on the activities of the Myrotvorets Center:
In 2016, Myrotvorets published a hacked list of the journalists who received “accreditation” by occupation authorities of the so-called Luhansk and Donetsk people’s republics (“LNR” and “DNR”), Russian-run pseudo-states in the occupied territory of eastern Ukraine. G7 ambassadors to Kyiv in their joint statement expressed “deep concern” about massive disclosures of journalists’ personal data on the Myrotvorets website and urged on the Myrotvorets team to withdraw personal data from public access, Ukrainian President Petro Poroshenko joined the call, as well as local human rights organizations and, finally, the list was later removed.
The list was discovered in a hacked email box by a "DNR" official. It contained real names, emails, and phone number by the journalists and was valid.
Other portions of critics were against adding various Ukrainian politicians to the Myrotvorets database. For example, Mikheil Saakashvili was added when he illegally crossed the Ukrainian border as a leader of a 2017 campaign to impeach President Poroshenko.
Though, the NGO wasn't questioned about the validity of the hacked email dumps Myrotvorets had shared earlier.
Reactions
Only a few major Ukrainian media have reported about the information by the Myrotvorets Center on suspected foreign funding of the Zelenskyy campaign. Among them were TV channels NewsOne and Priamyi, the newspaper Fakty, internet media Bukvy, Gordon.
Meanwhile, prior to the publishing of the haked email dump and the details, the pro-Russian Internet media strana.ua posted an article "Tree hollow for elections: Poroshenko volunteers are preparing a stove-piping of fake letters by Zelenskyy" based on a "Facebook post by a user Andriy Slyvka," who suggested that Myrotvorets had allegedly registered a network of fake email addresses, "tree hollows" in his terms, to maintain fake correspondence between "politicians," "FSB agents" and other fake addresses for a long period of time and then to imitate a hack and leaking of the fake messages. As we can see, this was pure speculation which has nothing in common with the leak that later followed.
As of now, two of the addressees of the Myrotvorets letter commented on the accusations brought by the Myrotvorets Center against presidential candidate Volodymyr Zelenskyy and his HQ. As we mentioned above, the SBU speaker said that her agency has received the materials and examines them. Meanwhile, RNBO has informed that it doesn't perform the operative and search activities and resent the Myrotvorets materials to SBU.
The third addressee, Verkhovna Rada's security committee, didn't issue any statements yet.
As well as there was no reaction from the accused side.
Update 2019/04/17:
By now, Euromaidan Press didn't receive any response from the Zelenskyy team. Though, there are updates on the issue:
- Head of the "Union of Donbas Volunteers" (SDV) Alexandr Boroday has confirmed that Khavchenko's email box was hacked. Though he calls the emails connected to the alleged funding of Zelenskyy's campaign "a provocation of SBU." Boroday heads the SDV while Khavchenko is a head of its Crimean outlet and Pinchuk leads its Moscow office.
- On 16 April, the SBU confirmed that it's been examining the data published by Myrotvorets.
- The Russian online newspaper "The Insider" has examined the facts surfaced by Myrotvorets, here are some highlights from their article:
- the email address [email protected] really belongs to Pinchuk since it's mentioned in one of his old resumes;
- The Insider found the metadata of the letters don't contain any indications that the letters were forged;
- talking to The Insider, Khavchenko said that he doesn't want comment on the matter of sending money to the Zelenskyy's HQ;
- The Insider couldn't contact Pinchuk;
- Zelenskyy's press service told to The Insider that they consider "all this a 100% fake, primary source of which is Myrotvorets."
- RBC's investigation called Konstantin Malofeyev the real owner of WEX cryptocurrency exchange, though he himself denied it. Earlier Boroday worked as a PR manager of Malofeyev.
Read also:
- Ukrainian NGO collects data on 1,500 Russian “Wagner” mercenaries in Operation Trust remake
- Ukrainian leak of data of journalists accredited in separatist “DNR,” explained
- Website PSB4UKR.ORG collects information about Putin’s terrorists
- Russian participation in the war in Donbas: evidence from 2017
- Interactive map shows origins of Russian mercenaries fighting in Donbas
- “DNR’s” propaganda apparatus exposed. Part 1: “Russophobe, get him out of Donetsk”
- 50,000 Russian citizens fought in Donbas war in first two years, their ex-leader says
- “We have no need for CIA help” – Ukrainian hackers of #SurkovLeaks