Secondary Infektion
Secondary Infektion, a long-running Russian information operation, was first revealed in 2019 as the Atlantic Council’s Digital Forensic Research Lab (DFRLab) analyzed the activities of 16 fake accounts emanating in Russia that were taken down by Facebook in May. The researchers uncovered the large-scale influence operation that involved scores of fake accounts writing in nine languages on over 30 social media and blogging platforms.
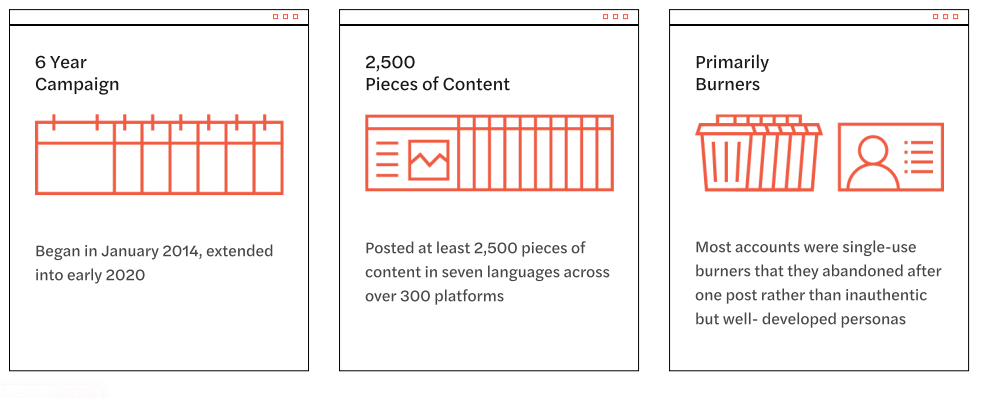
Graphika went deeper and from November 2019 to May 2020 found the traces of the Secondary Infektion activities spanned over 300 online platforms, from industry giants such as Facebook, Twitter, Youtube to “niche discussion forums in Pakistan and Australia.” In total, the researchers uncovered over 2,500 pieces of content posted across six years.
According to Graphika, Secondary Infektion is “a series of operations run by a large-scale, persistent threat actor from Russia” that worked in parallel to the Internet Research Agency (IRA, better known as Putin ally Prigozhin’s “troll factory”) and the GRU but was systematically different in its approach. The central entity behind multiple campaigns on social media “was already active in 2014 and was still running in early 2020.”
Key finds
According to Graphika’s report, the activities of the group began in January 2014 and extended into early 2020.
Rather than inauthentic but well-developed personas like those typically used by Prugozhin’s trolls, most accounts used to spread “Secondary Infektion” content were “single-use burners” abandoned after one post.
Researchers also found that the group was active on campaigns such as the elections in the US in 2016, France in 2017, and in Sweden in 2018. And it was part of the Russian efforts to discredit the World Anti-Doping Agency.
What made this group different from IRA and GRU is that it consistently used sophisticated techniques to cover its tracks while trying to achieve any measurable engagement.
Key narratives and targets
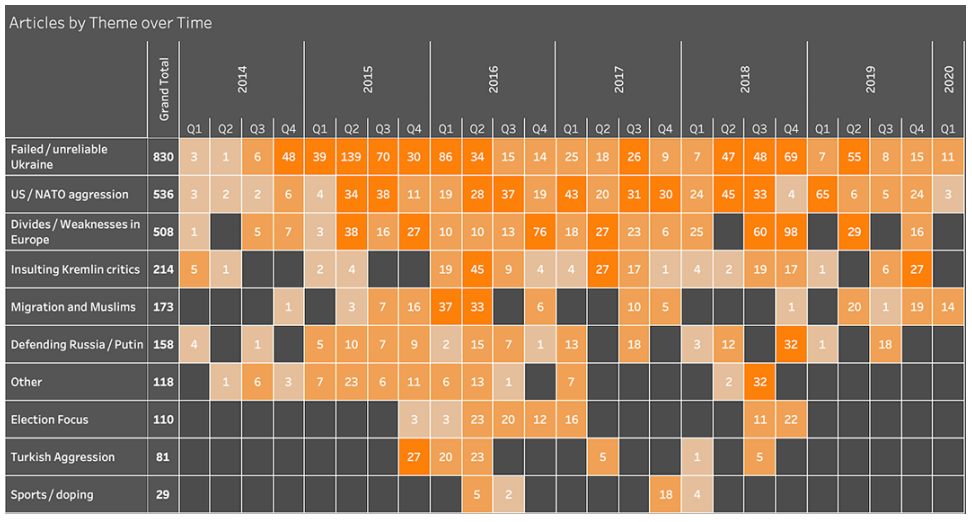
Secondary Infektion wasn’t a static campaign and its subjects shifted over time, however, the report stresses, “Ukraine was a perennial target.”


Graphika identified nine main topics among the narratives pushed by Secondary Infection which happened to be widely present among those surfacing in the Russian propaganda outlets,
- Ukraine as a failed or unreliable state.
- US and NATO aggression or interference in other countries.
- European divisions and weakness.
- Elections.
- Migration and Islam.
- Russia’s doping scandals in sporting competitions.
- Türkiye as an aggressive, destabilizing force.
- Defending Russia and its government.
- Insulting Kremlin critics including Alexei Navalny and the Bellingcat investigative group.
Forged documents
The report says that Secondary Infektion stands out “for its routine use of forged documents, sometimes surprisingly poorly crafted.” None of the other actors used this tactic with such volume and persistence. The researchers identified over 250 suspected forgeries that impersonated various Western leaders.
1/2 Рунетом гуляє погано сфабрикований "лист",в якому нібито прошу США допомогти перенести референдум у Нідерландах. pic.twitter.com/PkR5nBidQH
— Наталія Яресько/Natalie Jaresko (@n_jaresko) March 28, 2016
Tweet by Natalia Jaresko correcting the formatting of another Secondary Infektion forgery and calling out its poor English.
”It included fake letters, tweets and blog posts from leaders and officials including US Secretary of State Mike Pompeo, former White House Chief of Staff General John Kelly, various members of the US Senate Foreign Affairs and Intelligence Committees, representatives of the German, British, and Ukrainian governments, and former national leaders including Carl Bildt (Sweden) and Mikheil Saakashvili (Georgia),” the report reads.
Here are a few examples of forgeries mentioned in the study:


However, the report names only one effort of the campaign that really had an impact on the mainstream discussion of the countries it targeted: “the leak of apparently genuine US-UK trade documents on the eve of Britain’s general election in 2019, as exposed by [Graphika] in November 2019.”
The actor
The researchers didn’t find a confirmed attribution of Secondary Infektion to a specific group which poses a number of unanswered questions about the identity, goals, capabilities of the threat actor behind the operation.

However, the more general attribution to the Russian origin of Secondary Infection has multiple indicators “both technical and contextual.” For example, Facebook first attributed a set of accounts to Russian actors in May 2019, so did Reddit in the case of the US-UK trade leaks.
The initial target of the operation at its very beginning was the Russian opposition, then it shifted focus to Ukraine just when Russia invaded Crimea and unleashed war in the Donbas.
“The content of the campaigns closely mapped Russian preoccupations. The most striking example is the way that Secondary Infektion suddenly began attacking Türkiye after Türkiye shot down a Russian jet: the downing happened on November 25, 2015, and Secondary Infektion’s first attack on Türkiye came just one week later, on December 1,” the report reads.
Other topics also matched Kremlin’s narratives as well.
More clues came from the use of language with specific errors characteristic of Russian native speakers that would be insufficient for attribution alone, but can be viewed as a point of corroboration. Among the typical erors the report mentions,
“…difficulties with the use of “a” and “the,” as in the phrase “first the Europe, then the world,” difficulties with the word order in questions, as in “Why the truth is concealed?“, and difficulties with the possessive genitive, as in “3.15 million Germany’s new citizens.”









