Read our live updates of 27 June about the cyber attack: Ukrainian banks, enterprises, media and energy companies under powerful cyber attack, including Chornobyl NPP – LiveUpdates
On 27-28 June, an attack of malware infected computers worldwide, with the lion’s share of infections falling on Ukraine. Computers in the Ukrainian government, energy companies, banks, and media companies were infected, leading to data loss on many workstations and servers running Windows operating systems across the country. Many websites went offline, including the Government Portal. Trade on Ukraine’s three major stock markets, Perspektiva, PFTS, and Ukrainian exchange, was temporarily suspended. The Chornobyl nuclear power plant’s radiation monitoring system was also affected by the cyber attack.
The virus was initially dubbed Petya by malware experts due to its similarity to a ransomware used in attack in 2016. However, it was quickly discovered that the virus only masquerades as Petya while being more malicious: not only does it not unblock a user’s files after the “ransom” is paid, it wipes the hard disk of the computer altogether. This led security experts to consider another name for the virus: NotPetya, or ExPetr.
On 28 June, the Ukrainian state power distributor Ukrenergo was hit by a second cyber attack; however this time the effect was insignificant, according to Ukrenergo’s acting head.
Consequences
Ukraine’s Cyber Police reported that on 27-28 June 1508 persons and companies informed the police of having their computer equipment blocked by an encrypting virus. 178 of them submitted reports, including 152 private organizations and 26 state institutions. Other contacted the police for consultations.
As Ukrainian corporate networks were hit, the virus wreaked havoc on firms around the world as it spread to more than 60 countries.
How it works
As other ransomware, Petya encrypts files on the infected computer to demand a ransom to get a key for decrypting the files. But unlike other malware of this type, it also overwrites the Master Boot Record (MBR), rendering the machine unusable, and encrypts disk partitions, preventing users from recovering any information from the hard drive. NotPetya shares this functionality with Petya. The NotPetya’s ransom note urged a user to send $300 equivalent to a Bitcoin wallet:

But there was a significant difference of Petya from NotPetya. Petya generated a so-called installation key which could be used for decrypting the data; NotPetya generates a random set of characters instead of a valid key, making the decryption impossible.
Being activated on a computer, NotPetya attempts to get the administrator’s credentials and infect other computers on the local network, using not just the leaked NSA exploit known as EternalBlue but also standard remote administration tools to spread. This is so-called worm functionality, the capability to infect the network computers.
Detailed technical information on NotPetya is available on computer security sites: Symantec, Microsoft Technet, Eset, Avast, Avira, AVG.
Initially, the auto-update mechanism of the Ukrainian tax and accounting software package, MEDoc, was used to break into computers. MEDoc’s auto updater downloaded and ran a fake update, causing the malware installation.
MEDoc is widely used only in Ukraine. This fact indicates that organizations in this country were the primary target.
“Our servers are under a virus attack,” MEDoc reported on its site on 27 June, but later the statement was removed. The Intellect Service company, the developer of MEDoc, admitted that the cyber attack put their document flow server down, as well as their online accounting service Sota. But the company denies that their update servers were the initial source of the attack.
Microsoft Technet states that MEDoc ran the chain leading to the malware installation:
We observed telemetry showing the MEDoc software updater process (EzVit.exe) executing a malicious command-line matching this exact attack pattern on Tuesday, June 27 around 10:30 a.m. GMT. The execution chain leading to the ransomware installation is represented in the diagram below and essentially confirms that EzVit.exe process from MEDoc, for unknown reasons, at some moment executed the following command-line:
C:\\Windows\\system32\\rundll32.exe\” \”C:\\ProgramData\\perfc.dat\”,#1 30The same update vector was also mentioned by the Ukraine Cyber Police in a public list of indicators of compromise (IOCs) , which includes the MEDoc updater.
Symantec has also confirmed that MEDoc was used for the initial insertion of Petya into corporate networks.
Why did the intruders choose MEDoc?
The software is widely used only in Ukraine and it is coded in such way that even the official dealers who sell MEDoc recommend users to add MEDoc to exceptions lists of the antivirus software because of endless false positive antivirus detections. If you run a process from under MEDoc, you probably bypass the installed antivirus software.
The second wave of attack was spawned by a phishing campaign, the emails of which contained an infected Microsoft Word document.
Here is another phishing email message and the tech info on Petya. The attack *was* targeted https://t.co/f2af4pqLEU pic.twitter.com/9IZg5UXKk4
— English Luhansk (@loogunda) June 27, 2017
One more way used by intruders was so-called watering hole attack, targeted distribution of the malware via infected websites. At least one infected site was found in Ukraine which distributed NotPetya:
In addition to known vectors, ExPetr/PetrWrap/Petya was also distributed through a waterhole attack on https://t.co/j9DvYcEgW7
— Costin Raiu (@craiu) June 28, 2017
Petya or NotPetya?
At first, since the behavior of the malware was similar, there were suggestions that the cyber attack was conducted using a modified WannaCry virus. Later, computer security experts identified the virus as Petya, a ransomware known since 2016. Antivirus companies dubbed it Petya.A, Petya.D. Later researchers pointed out that Petya, used in the attack on Ukraine, is not really a ransomware, but rather a wiper just masquerading as the Petya ransomware. The wiper is a type of malware destroying data on the target’s hard disk. That is why antivirus companies gave it new names — NotPetya, PetrWrap, or ExPetr.
Cyber security expert Matt Suiche from Comae Technologies analyzing the behavior and the reversed code of NotPetya came to a conclusion: “the ransomware was a lure for the media, this variant of Petya is a disguised wiper.” He wrote:
2016 Petya modifies the disk in a way where it can actually revert its changes. Whereas, 2017 Petya does permanent and irreversible damages to the disk.
Later, Kaspersky Lab‘s research led to a similar conclusion. Symantec says the same:
[Once ecrypted] the disk can never be decrypted. This demonstrates that Petya is more accurately a wiper rather than ransomware.
Computer security veteran The Grugq also favored the same opinion, “Although there is significant code sharing, the real Petya was a criminal enterprise for making money. This [latest malware] is definitely not designed to make money. This is designed to spread fast and cause damage, with a plausibly deniable cover of ransomware.”
This means that even if victims would pay the ransom they will be not able to get their data back. And this means getting ransom wasn’t the primary goal of the attack.
Myths behind the attack
“It was a ransomware”
As Matt Suiche noted, “The fact of pretending to be a ransomware while being in fact a nation-state attack — especially since WannaCry proved that widely spread ransomware aren’t financially profitable — is in our opinion a very subtle way from the attacker to control the narrative of the attack.”
“Russia was the #2 affected country with about half number of Ukraine’s infections”
As of June 27 evening, Russia wasn’t even mentioned in Eset’s Top-8 of the countries most affected by NotPetya attack:
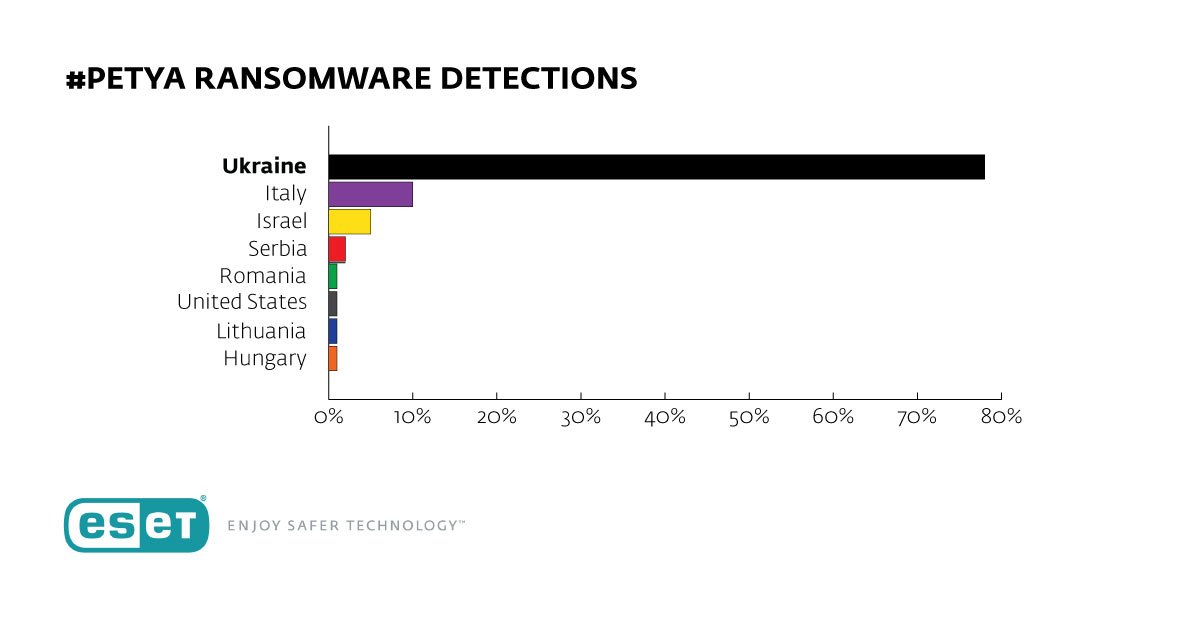
Two days later, Ukraine remained on top (75,24%), Russia emerges in 7th place with only 0,82% in Eset’s stats:

According to the graph by Symantec Corporation published on June 27, Russia was third:

Moscow-based Kaspersky Lab antivirus company published their own graph on 27 June. According to the data of the Russian company, Russia was in second place among the countries hit by NotPetya malware, sharing about a half of Ukraine’s 60% of infections worldwide:

- US Senators sought to ban Moscow-based cybersecurity software company Kaspersky Lab out of concern they “might be vulnerable to Russian government influence,” according to Reuters.
On the same day
On 27 June before the cyber attack, a top Ukrainian military intelligence officer was killed in a car blast in Kyiv. In the evening of the same day, a colonel of Ukraine’s Security Service was killed in another car blast in Donetsk Oblast. There also was an unconfirmed report about one more plotted car blast in Khmelnytskyi to assassinate an army officer.
“It’s no accident that the terrorist act [killing a military officer in Kyiv] coincided with a massive cyber attack, which also has a Russian trace,” Oleksandr Turchynov, secretary of the National Security and Defense Council of Ukraine, said.
Petya is a diminutive form of the name Peter (Petro in Ukrainian). The Russian press openly calls the cyber warfare “the virus named after Poroshenko“, however, they suppose Russia couldn’t conduct the attack because “Russia was also hit.”
The cyber attack targeted primarily Ukrainian infrastructure, businesses, and authorities, using vulnerabilities of the software package used only in Ukraine for the initial spread.
All indirect indications are that Russia did it as part of the hybrid war against Ukraine. However, there is still no evidence of Russia’s direct involvement in at least 3 attacks on Ukraine on 27 June, the two car blasts and the massive cyber attack.
- The NotPetya cyber attack didn’t affect the largest bank in Ukraine, PrivatBank. The bank’s entire computer infrastructure, from ATMs and workstations to servers, is built on Linux operating system. In the wake of the last attack, Privatbank now proposes to help state bodies, institutions, enterprises migrate to Linux.
- On 12 May 2017, Ukraine was among the countries most affected by WannaCry ransomware attack.
Read more:
- Ukrainian banks, enterprises, media and energy companies under powerful cyber attack, including Chornobyl NPP – LiveUpdates
- Ukrainian Security Service colonel killed, three wounded in car blast in Donbas
- Car explosion in Kyiv takes life of Ukrainian Colonel; involvement of Russian special services suspected
- No more VPNs: Kremlin mulls limiting anonymising software
- Moscow expanding its cyber war against Ukraine
- Deception, Disinformation, and Doubt: Hybrid Warfare in Eastern Ukraine
- Putin conducts his foreign policy like a special op, Melnikov says
- Beware of Russian Cyber Warfare in 2016
- Cyber attacks have not hindered elections — SBU
- Perfection as a weapon of hybrid warfare
- Ukrainian cyber army extracted personal data of Strelkov’s terrorist group









