After massive attacks on Ukraine's military and civilian infrastructure, the Kremlin appears to have targeted another area - Ukraine's cybersecurity. The first victim was a large-scale attack on Ukraine's biggest mobile operator Kyivstar, which has unsuccessfully tried to restore services for several days, leaving millions of users without connectivity and internet access.
Adding to Ukraine's mounting challenges is a disturbing revelation: Russian special services may have had unrestricted access to surveillance camera footage across the country for years. This stems from the use of the Russian software TRASSIR in many surveillance systems, sending data to servers in Moscow.
In response to Russia's invasion, Ukraine blocked access to millions of Russian IP addresses, including TRASSIR's servers. However, a concerning loophole persists - users can still access the software through VPNs, redirecting video streams to Moscow servers. Investigative journalists from the Skhemy program at Radio Free Europe/Radio Liberty uncovered these vulnerabilities, emphasizing the urgent need for strengthened cybersecurity measures in Ukraine. We have summarized their findings for you.
What is TRASSIR?
TRASSIR, developed by the Russian company DSSL, has been in use for two decades. The company operates in numerous countries worldwide and, as claimed on its website, boasts a clientele of 400,000 customers.
Importgenius, an Arizona-based company specializing in trade data, reports that over 10,000 cameras and video recorders with this Russian software entered Ukraine since 2016, with the latest shipments in February 2022.
These acquisitions were by state entities, including critical infrastructure sites. Notably, TRASSIR cameras were present at the Chornobyl nuclear power plant, seized by Russians on the war's first day. Additionally, they were widely adopted by private businesses and citizens.
The Russian software facilitates comprehensive monitoring, including facial recognition, vehicle tracking, and license plate identification. Concerningly, Skhemy revealed that TRASSIR cameras and their embedded software could potentially send data to Russian servers, raising the risk of collecting information on military movements via railways and highways.
TRASSIR's alarming link to Russian servers
The Skhemy team examined one of the cameras with experts from two specialized Ukrainian companies, the Computer Forensics Laboratory and the Digital Security Lab. They revealed that while the camera was made in China, its software is entirely Russian. This suggests that video from these cameras first goes to Moscow servers owned by FSB-associated companies before reaching consumers' phones or computers.
"We see this camera is sending requests to a subdomain of the manufacturer's website, TRASSIR - m30.ru.cloudtrassir.com. The domain name resolves to an IP address that is identified as being Russian, with a geolocation in Moscow. This indicates the camera's connectivity relies on servers under Russian control," said Natalia Onyshchenko, a web security specialist at the Digital Security Lab.

In the experiment, experts identified several such IP addresses, and a de-anonymization service revealed these servers are in Moscow. Essentially, video from a camera with TRASSIR software doesn't go directly to the connected device, like a phone; it first passes through Moscow servers.
Who owns the Russian servers collecting data from Ukraine?
Journalists identified two companies that own these servers. One of them is the telecommunications company Digital Network, whose clients include Russia's largest search engine, Yandex, and the federal TV channel Zvezda. The other is VK Company, which owns the Russian social network Odnoklassniki, banned in Ukraine, and the Mail.ru email service. Both firms are closely tied to Russia's Federal Security Service (FSB) and the Ministry of Internal Affairs.
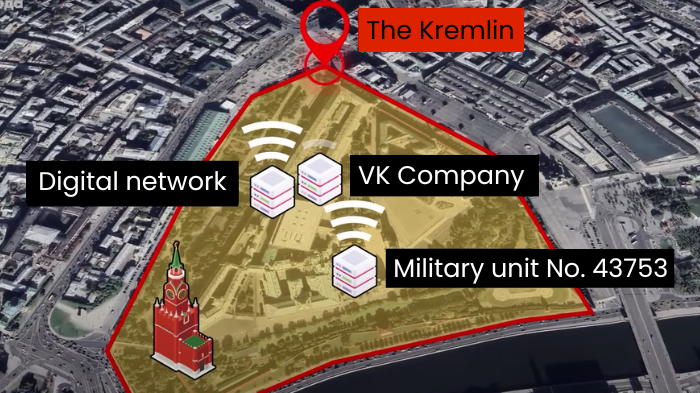
In particular, between 2015-2017, Digital Network provided internet connectivity to military unit No. 43753, which houses the FSB Center for information security and special communications.
"Everything related to information, the internet, and communication - all of this has been consolidated in that center. That is, it is involved in using the internet to carry out certain special information operations," stated Major General Viktor Yagun, retired from the Security Service of Ukraine.

Back in 2016, Russian human rights activists reported that Russia's special services have unfettered access to the servers of social networks, specifically VKontakte and Odnoklassniki. Court rulings in Russia evidenced this.
"Russian legislation allows intelligence and law enforcement agencies access to all resources stored in Russia, even without court orders," stated Yagun.
TRASSIR at Chornobyl and in Municipal Councils
The Chornobyl nuclear power plant has been using the TRASSIR video surveillance system since at least 2011, and it continued to receive Russian TRASSIR software even after the annexation of Crimea in 2014. Initially denying the presence of TRASSIR, The Chornobyl nuclear power plant later admitted to having Russian software confined to a local network without internet access. In 2023, they claimed to have removed TRASSIR software.
Trending Now
"The placement of this camera at a critical infrastructure site raises questions about what the owners of that server see and how they utilize that information for military purposes," stated Sergey Denisenko, the director of the Computer Forensics Lab.

The Poltava City Council, acquiring TRASSIR software with over 300 attached cameras, has kept these cameras operating on Russian software. They argue that information does not reach servers in Russia but are actively seeking funds to update the surveillance system without Russian software.
The Ukrainian Prozorro system revealed tenders for TRASSIR software maintenance with various state entities, including the Administration of Sea Ports of Ukraine, municipal councils in Kharkiv, Kherson, and Nikopol, the Maritime Search and Rescue Service in Odesa, and others, using Russian software.
Ukrainian businesses used TRASSIR, too
Major Ukrainian companies previously procured Russian TRASSIR software and cameras. These companies include the sunflower oil producer Kernel, global steel pipes and railway wheels producer Interpipe, P&G Ukraine, postal and courier company Nova Poshta, TV channel 1+1, real estate developers KAN Development and Ukrbud, prominent appliance stores like Allo, Citrus, and Eldorado, as well as the IMAX cinema chain, previously procured Russian TRASSIR software and cameras. Most owners now claim to have ceased their use, including Eldorado and Citrus.
Nova Poshta confirmed using TRASSIR software for recorders until 2019, emphasizing no internet connection. They mentioned that some branches have still had unsupported TRASSIR recorders since 2019.
Claims and contradictions: TRASSIR EU denies wrongdoing
The primary seller of Russian equipment and software in Ukraine, TRASSIR EU, stated that they have not been working with the Russian company DSSL since April 2023.
"The TRASSIR brand is registered in Ukraine, as evidenced by records in the relevant registries," stated Olena Semeniuk, the accountant for the company. "The software was owned by Ukrainian citizen Oleh Kiyashko, who had registered the copyright."
Yet, journalists found that Oleh Kiyashko holds Russian citizenship. In 2021, he renewed his passport and updated his information as an individual entrepreneur in Moscow, according to the record in the Russian register of legal entities.

Ukraine blocks Russian IPs, yet TRASSIR access persists via VPN
On 27 February 2022, four days after Russia's full-scale invasion, The State Special Communications Service of Ukraine blocked access to millions of Russian IP addresses, including TRASSIR's servers. However, users can still access this Russian software through a VPN, redirecting the video stream to Moscow servers.
In May 2022, amidst the ongoing war, The State Special Communications Service of Ukraine warned government agencies about the collaboration between the company TRASSIR/DSSL and Russian federal ministries and security services.
The State Special Communications Service mentioned examining TRASSIR equipment and software in 2019, with undisclosed findings. The Security Service of Ukraine (SBU) noted their attention to this software as early as 2020, but journalists report minimal impact on the situation.
There remains a risk of TRASSIR re-entering the Ukrainian market as a foreign product, particularly AziGuard from the Romanian company AziTrend, which features TRASSIR software. The Ukrainian supplier TRASSIR EU is already cooperating with them.
Read more:





