A powerful cyber attack on Ukrainian banks, energy companies is underway. Reportedly, another WannaCry-like ransomware cryptoworm software is used to attack computers. The malware crypts all non-executable files on computers running Microsoft Windows operating system and demands ransom payments in the Bitcoin cryptocurrency. According to various sources, the companies under attack are: Oshchadbank state bank, energy companies – Dniproenergo, Zaporizhzhiaenergo, Kyivenergo, delivery company Nova Poshta, Ukrposhta state mail company, media holding TRK Luks managing 24 Kanal TV channel, Radio Luks, Radio Maksymum and other companies and organizations.
- Cabinet of Ministers of Ukraine
- Oshchadbank state bank
- energy companies – Dniproenergo, Zaporizhzhiaenergo, Kyivenergo,
- delivery company Nova Poshta,
- Ukrposhta state mail company,
- media holding TRK Luks, affiliating 24 Kanal TV channel, Radio Luks, Radio Maksymum,
- News site Korrespondent.net
- ATR TV channel
- Boryspil International Airport
- The sites of the National Police and the Cyber Police
Update 17:09: As of the data we have at this moment, a targeted mass-mailing attack was performed around 15:00. The email messages contained a ransomware. The virus is called Petya.A named probably after the diminutive form of the name Petro. The ransomware target computers running the Microsoft Windows operating systems. Preliminary, the virus encrypts not the files of certain types as WannaCry malware did, but the entire partitions of the hard drive. Most of the desktop computers and many servers in organizations and enterprises in Ukraine use Windows operating systems by Microsoft.
It is not the first cyber attack on key infrastructure objects in Ukraine. In December 2016, several districts of Kyiv and neighboring districts of Kyiv Oblast left without electricity, head of Ukrenergo energy company Vsevolod Kovalchuk said that “external interference in the data transfer systems” caused the blackout.
National Bank reports an “external cyber attack”
The National Bank of Ukraine warns banks and other companies in financial sector about an “external cyber attack using unknown virus” on several Ukrainian banks, as well as on commercial and state enterprises. the attack is underway today. The attack caused issues for the banks while serving customers, performing bank operations.
Update 16:18: Oshchadbank state bank has reported in their official statement that due to a hacker attack on a string of Ukrainian companies and banks, Oshchadbank had to limit “the functionality of services for clients”. According to reports on social networks, Oshchadbank ATM machines don’t service clients for now. The bank recommends using ATMs of other banks. According to reports on Twitter, national supermarket chain ATB doesn’t accept Oshchadbank cards today.
Update 17:27: Other banks hit by the attack were Pivdennyi, TASkombank, OTP Bank, and the state-owned Ukrgazbank, UNIAN reports.
Energy companies
According to Obozrevatel referring to their own source, “99% of computers in Zaporizhzhiaoblenergo, Dniproenergo and Dnipro electric energy system are blocked (encrypted)”.
Update 16:44: Kyivenergo and Ukrenergo energy companies were also under attack.
Media companies
TRK Luks media holding has reported a “devastating virus attack” that hit their offices in Kyiv and Lviv. The holding affiliates popular TV channel 24 Kanal, and radio stations Radio Luks, Radio Maksymum.
At 14:17 journalist Denys Bihus reported in his post on Facebook the blackout of 24 Kanal and both radio stations.
Popular Internet media korrespondent.net is down since about 15:00 by now (16:06).
Update 16:53: Journalist Ayder Muzhdabaev has published a photograph of an infected computer in the office of Crimean Tatar ATR TV channel. His comment was, “A greeting from RF [the Russian Federation] has also come to ATR office. UPD: The channels keeps broadcasting”:
https://www.facebook.com/ayder.muzhdabaev/posts/1583604485006754
Delivery services
As of now, 15:53, the official site of Ukrposhta state mail company is inaccessible.
All outlets of Nova Poshta delivery company have suspended service, Ukrainska Pravda reports. “Nova Poshta” reports the “massive attack by the Petya.A virus” on the information systems and the contact center of the company in Kyiv. This “temporary disabled the customer service” of the company.
Official institutions
Update 16:40: The sites of the National Police and the Cyber Police are inaccessible and served from the cache as of 16:40:
Transport
Update 16:48: Head of Boryspil International Airport wrote on his Facebook page that the airport and “several state enterprises” came under a “spam attack”.
Live Updates
Update 17:38: Ukrtelecom telephone company was attacked, it continues providing internet and telephony, however, its call center and computers of the service center are down, according to the post on the company’s official page on Facebook:
https://www.facebook.com/Ukrtelecom/posts/1807429992617050
Update 17:43: Banking cards are not accepted for payments at Kyiv Metro:
Even Kyiv metro is under cyber attack. Payments by banking cards aren't accepted https://t.co/eRUJxDpmTg via @Kateryna_Kruk pic.twitter.com/rhAUGjmHct
— Liveuamap (@Liveuamap) June 27, 2017
Update 17:52: Petrol station chain KLO is “blocked by the virus attack”, the official KLO Facebook account reported:
https://www.facebook.com/klo.oil/posts/1727782583906123:0
Update 17:58: The Presidential Administration reports that its information systems and the cyber defense team “operate in the normal mode”:
Deputy Head of the Presidential Administration @dshymkiv instructed the team to help IT teams of other governmental institutions pic.twitter.com/iQw33ZJO7X
— The Bankova (@TheBankova) June 27, 2017
Update 18:01: A photo of an infected computer reportedly taken at 14:45 at the Lenin plant in Babruysk, Belarus was published on Twitter:
Завод им. Ленина в Бобруйске 15 минут назад. Вроде как вся сеть. pic.twitter.com/Q2AqcCT7bU
— Pretensjonalny bóbr (@dmrlx) June 27, 2017
Update 18:30: The official Twitter account of Ukraine responded to the cyberattack, “Some of our gov[ernment] agencies, private firms were hit by a virus. No need to panic, we’re putting utmost efforts to tackle the issue”, “this is fine” meme has been attached to the message:
https://twitter.com/Ukraine/status/879706437169147906
Update 18:39: Ukraine’s Prime Minister Volodymyr Groysman called the attack “unprecedented” but added that “vital systems haven’t been affected”:
KIEV, Ukraine (AP) — #Ukraine's prime minister says cyberattack 'unprecedented' but 'vital systems haven't been affected'
— Matt Lee (@APDiploWriter) June 27, 2017
Update 18:41: Ukraine’s Ministry of Finance reported, “[Information] systems of MinFin are operating. Our IT guards reacted fast and effectively,” and added in English, “Stay away, dear hackers, stay away.”
Update 18:48: PM Volodymyr Groysman’s tweet at 18:44: “Just now the Government Portal resumed operation. It is the first positive signal. The work continues to localize the virus and overcome the consequences of the cyber attack”
Щойно Урядовий портал відновив роботу. Це – перший позитивний сигнал. Триває робота з локалізації вірусу та подолання наслідків кібернападу
— Volodymyr Groysman (@VGroysman) June 27, 2017
Update 19:16: The British WPP company has reported that IT systems in its several companies have been affected by a suspected cyber attack:
IT systems in several WPP companies have been affected by a suspected cyber attack. We are taking appropriate measures & will update asap.
— WPP (@WPP) June 27, 2017
Update 19:24: Chornobyl’s radiation monitoring system has been affected by the cyber attack, AFP reports citing the spokeswoman.
An ATM in Kyiv:
https://twitter.com/sioburn/status/879721166742704130
Update 19:50
Danish Maersk company says its IT systems are down due to a cyber attack.
Executive director of the Europol Rob Wainwright says, “We are urgently responding to reports of another major ransomware attack on businesses in Europe.”
Europol reports:
We are aware of a dvlping ransomware attack & liaising w/ cyberunits in EU & key industry partners to establish full nature of this attack.
— Europol (@Europol) June 27, 2017
Update 20:08 The Russian oil giant Rosneft was also hit, Norway’s National Security Authority said an “international company” there was affected, according to the Washington Post.
Update 20:31: The diagram published by the Russian Twitter account of Eset antivirus company clearly shows that Ukraine was the target of the cyber attack, the text commenting the diagram reads, “Rating of the countries most affected by Petya [virus]. The infection has started from Ukraine”:
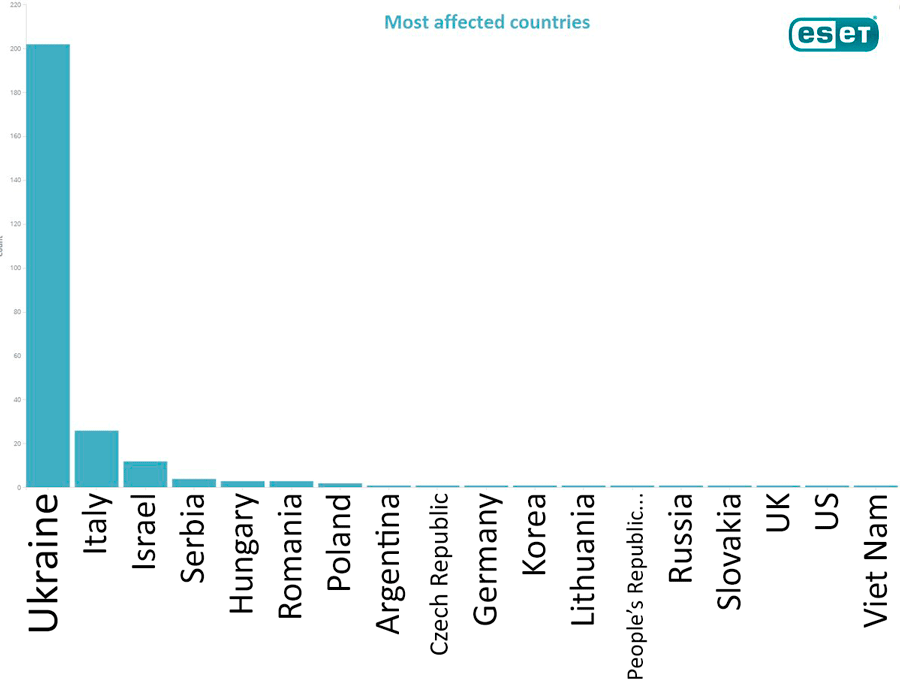
Update 21:54: According to DefenseOne, the malware quickly infected nearly 300,000 computers worldwide. The virus uses two software exploits released in April by the hacking group called the Shadow Brokers.
Update 21:57: Earlier today, Deputy PM Pavlo Rozenko published a photograph of an infected computer with comment, “Ta-dam! It seems the computers at the Cabinet of Ministers of Ukraine have been knocked out. The network is down.”
Та-дам! Секретаріат КМУ по ходу теж "обвалили". Мережа лежить. pic.twitter.com/B74jMsT0qs
— Rozenko Pavlo (@RozenkoPavlo) June 27, 2017
Update 22:06: The Cyberpolice wrote, “It is preliminary found that the first virus attacks on Ukrainian companies could [be conducted] due to vulnerabilities of M.E.Doc [accounting] software”:
Кіберполіцією попередньо установлено, що перші вірусні атаки на українські компанії могли виникнути через вразливості ПЗ M.E.doc. pic.twitter.com/MXV7ODtaoM
— Cyberpolice Ukraine (@CyberpoliceUA) June 27, 2017
Developer of M.E.Doc, Intellect Service company says "at the moment of update sys couldn't be infected fr/upd file" https://t.co/JKAWFkRyG5
— Euromaidan Press (@EuromaidanPress) June 27, 2017
Update 22:31: The list of organizations and companies affected by the attack of Petya.A virus, according to CensorNet:
Cabinet of Ministers of Ukraine
Interior Ministry of Ukraine
Ministry of Culture
Ministry of Finance
National Police (including regional websites)
Cyberpolice
Kyiv State City Administration
Lviv City Council
Ministry of Energy
National BankBanks
Oshchadbank
Sberbank
TASKomertsbank
Ukrhazbank
Pivdennyi
ОТР Bank
KredobankTransport companies
Boryspil International Airport
Kyiv Metro
Ukrzaliznytsia (major railway carrier)Media
Radio Era-FM
Football.ua
STB
Inter
Pershyi Natsionalnyi
Telekanal 24
Luks Radio
Maksymum Radio
KP in Ukraine
ATR TV channel
Korrespondent.net
Large companies
Nova Poshta
Kyivenerho
Naftogaz Ukrainy
DTEK
Dniproenerho
Kyivvodokanal
Novus
Epicentr
Arcelor Mittal
Ukrtelekom
UkrposhtaCell phone operators
Lifecell
Kyivstar
Vodafone UkrainePharmacy/Hospitals
Farmak
Borys Medical Center
Feofania
Arterium CorporationGas stations
Shell
WOG
Klo
TNKForeign companies
Rosneft
Update 22:47: The State Service of Special Communication and Information Protection of Ukraine (Derzhspetszvyazku) reports that control of the situation has been currently taken. No state e-resource secured by common cyberdefense contour, released by Derzhspetszvyazku in the System of protected Internet access, was affected. Electronic state registries “were not damaged and didn’t sustain any other unauthorized operations.”
Update 23:02: Computer security expert Amit Serper says he has found a way to prevent the Petya malware from running:
https://twitter.com/0xAmit/status/879778335286452224
100% certainty! Create a file called perfc with no extension in %windir%. And now I celebrate with friends! pic.twitter.com/JB03xab2BZ
— Amit Serper (@0xAmit) June 27, 2017
Update 23:53: The unprecedented cyber attack of Petya/Petya.A/Petrwrap ransomware on Ukraine got mass сoverage in world media. Here are some of the stories published in the world press:
- Ukraine cyberattack widens to hit multinationals — Deutsche Welle
- Petya cyber attack: Ransomware spreads across Europe with firms in Ukraine, Britain and Spain shut down — The Teleegraph
- Ukraine reacted to the biggest hack in its history with a GIF of a dog in a room on fire “This is fine.” — Vox
- Putin Uses a Wave of Cyber-Attacks and a Political Assassination in Ukraine to Send a Message to the West — Tablemag
- ‘Petya’ Cyberattack Hits Ukraine, And Experts Say It’s Spreading Globally — NPR
- Ukrainian Banks, Electricity Firm Hit by Fresh Cyber Attack — New York Times
- Widespread Cyberattack Hits Major European Companies — NBCnews
- Massive cyberattack targets Europe, US — MoneyCNN
- New cyberattack spreads fast across Ukraine, Europe — CBS News
- Cyber attack hits global businesses and Ukraine government — Financial Times
- Global ransomware attack causes turmoil — BBC
- Ukraine cyber attack: Chaos as national bank, state power provider and airport hit by hackers — The Independent
- As Windows Virus Chaos Spreads, Ukraine Responds With Odd Choice of Meme — Newsweek
Update June 28, 00:03: According to Symantec antivirus company, Petya malware has been in existence since 2016. It differs from typical ransomware as it doesn’t just encrypt files, it also overwrites and encrypts the master boot record (MBR). In this 27 June attack, the ransom note is displayed on infected machines, demanding that $300 in bitcoins be paid to recover files.
Update 00:31: TrendMicro antivirus company has published the technical description of Petya ransomware, showing the system vulnerabilities it uses and disclosing its infection flow. Each user is asked to pay US$300 to decrypt the encrypted data and, according to TrendMicro, approximately US$7,500 had been paid into the Bitcoin address of the adversary as the article was published. However, the company notes, “We advice against paying the ransom–this is particularly true in this case, as the email account mentioned in the ransom note is no longer active.”
Update 00:58: On 27 June at 18:08 Kharkiv International Airport informed on its Facebook page that staff were manually checking-in passengers due to a hacker attack. Everything else was operating as per normal:
https://www.facebook.com/hrk.aero/photos/a.554780944552921.1073741828.552821788082170/1533337316697274/?type=3
Update 01:40: Jun27 afternoon, cashier checkout computers infected with Petya ransomware in a supermarket in Kharkiv, eastern Ukraine:
Супермаркет в Харькове pic.twitter.com/H80FFbzSOj
— Mykhaïlo Golub (@golub) June 27, 2017
Update 02:11: Former US ambassador to Russia, Michael McFaul has commented on the Petya cyber attack on Ukraine on his Twitter, “Shocking violation of Ukrainian sovereignty. I hope all world leaders who respect sovereignty will not only speak out but also act.”
Update 02:31: Petya ransomware reaches Australia, suspending operations at Cadbury’s Claremont factory:
#Petya ransomware has now reached #Australia.
via @techAU https://t.co/I3h4rUlAL4— Euromaidan Press (@EuromaidanPress) June 27, 2017
Update 02:57: McAfee antivirus company has published a detailed technical analysis of Petya ransomware. The malware uses three different mechanisms attempting to infect remote computers. The first mechanism is Eternal Blue exploit, used also by WannaCry ransomware. Two other mechanisms are using the standard Microsoft remote administering tool psexec.exe and using the Windows Management Instrumentation Command-line (WMIC) to execute malware the executive components directly on the remote machine. This means that one infected computer can infect all vulnerable computers in the local network including servers running Windows operating systems.
Updates finished for today, good night.
Read more:
- Moscow expanding its cyber war against Ukraine
- Deception, Disinformation, and Doubt: Hybrid Warfare in Eastern Ukraine
- “We have no need for CIA help” – Ukrainian hackers of #SurkovLeaks
- Ukrainian hackers publish Surkov’s plans to destabilize Ukraine in coming months
- Putin conducts his foreign policy like a special op, Melnikov says
- Russian-hybrid attack on civilians in Krasnohorivka is a form of psychological warfare
- Beware of Russian Cyber Warfare in 2016
- Cyber attacks have not hindered elections — SBU
- Perfection as a weapon of hybrid warfare
- Ukrainian cyber army extracted personal data of Strelkov’s terrorist group






